
It’s the beginning of Pride month. At VentureBeat, it’s also the beginning of a six-week-long deep dive into AI innovation, culminating in our 4th annual AI Innovation Awards.Read More

It’s the beginning of Pride month. At VentureBeat, it’s also the beginning of a six-week-long deep dive into AI innovation, culminating in our 4th annual AI Innovation Awards.Read More

Research reveals that 45% of cybersecurity professionals have considered quitting the industry due to stress.Read More

Helsinki, Finland, has one of the world’s longest-running digital twin programs. Now it is making strides, leading as an example for other cities that wish to do the same.Read More

Working through the Great Resignation: the CIO of Dating Group is sharing his company’s transition from in-office to remote.Read More

Enlarge (credit: Owl Labs)
The Meeting Owl Pro is a videoconference device with an array of cameras and microphones that captures 360-degree video and audio and automatically focuses on whoever is speaking to make meetings more dynamic and inclusive. The consoles, which are slightly taller than an Amazon Alexa and bear the likeness of a tree owl, are widely used by state and local governments, colleges, and law firms.
A recently published security analysis has concluded the devices pose an unacceptable risk to the networks they connect to and the personal information of those who register and administer them. The litany of weaknesses includes:
Researchers from modzero, a Switzerland- and Germany-based security consultancy that performs penetration testing, reverse engineering, source-code analysis, and risk assessment for its clients, discovered the threats while conducting an analysis of videoconferencing solutions on behalf of an unnamed customer. The firm first contacted Meeting Owl-maker Owl Labs of Somerville, Massachusetts, in mid-January to privately report their findings. As of the time this post went live on Ars, none of the most glaring vulnerabilities had been fixed, leaving thousands of customer networks at risk.

A data privacy vendor and a data virtualization provider integrate the logistics and policy of data access.Read More

Enlarge / Ford’s electric F-150 Lighting (L), eTransit (M), and Mustang Mach-E (R) battery-electric vehicles have all been such successes that they’re all sold out for the rest of the year. And that’s prompting the company to rethink how it goes about the whole process. (credit: Ford)
Few Americans enjoyed the car-buying process even before supply chain chaos, and the chip shortage led dealerships to mark up inventory by thousands of dollars. But buying a Ford electric vehicle might be a lot less painful in the future, if Ford CEO Jim Farley gets his way. On Wednesday, Farley said that he wants the company’s EVs to be sold online-only, with no dealer markups or other price negotiations, according to the Detroit Free Press.
“We’ve got to go to non-negotiated price. We’ve got to go to 100 percent online. There’s no inventory (at dealerships), it goes directly to the customer. And 100 percent remote pickup and delivery,” Farley said while speaking at a conference in New York.
One of Tesla’s most popular innovations was to eschew traditional dealerships and sell its products directly to customers. But traditional manufacturers like Ford are usually prohibited from selling their products directly to customers, a legacy of fears over vertical integration written into state laws during the early 20th century. As such, Ford’s franchised dealers will almost certainly still have a role to play.

Enlarge / Get busy imagining this logo on a box.
It has been nearly eight years since Dragon Age: Inquisition launched as the most recent full game in Bioware’s acclaimed RPG series and nearly four years since an unnamed sequel was first teased at the 2018 Game Awards. On Thursday, developer BioWare revealed an official title for that sequel—Dragon Age: Dreadwolf—and confirmed the game won’t be coming until 2023 at the earliest.
In a brief blog post, BioWare confirmed the new game will focus on antagonist Solas, the mysterious elven hedge mage who was introduced as the Dread Wolf in Inquisition. Solas was also central to that game’s 2015 Trespasser DLC and featured heavily in a four-minute Gamescom 2020 behind-the-scenes featurette on the game.
In its announcement, BioWare describes Solas as someone whose “motives are inscrutable and his methods sometimes questionable, earning him a reputation as something of a trickster deity—a player of dark and dangerous games.” The developer also insists that “if you’re new to Dragon Age, you have no need to worry about not having met our antagonist just yet. He’ll properly introduce himself when the time is right.”

The importance of healthy workplaces, security and conservation makes developing reliable AI-based smart building systems urgent.Read More
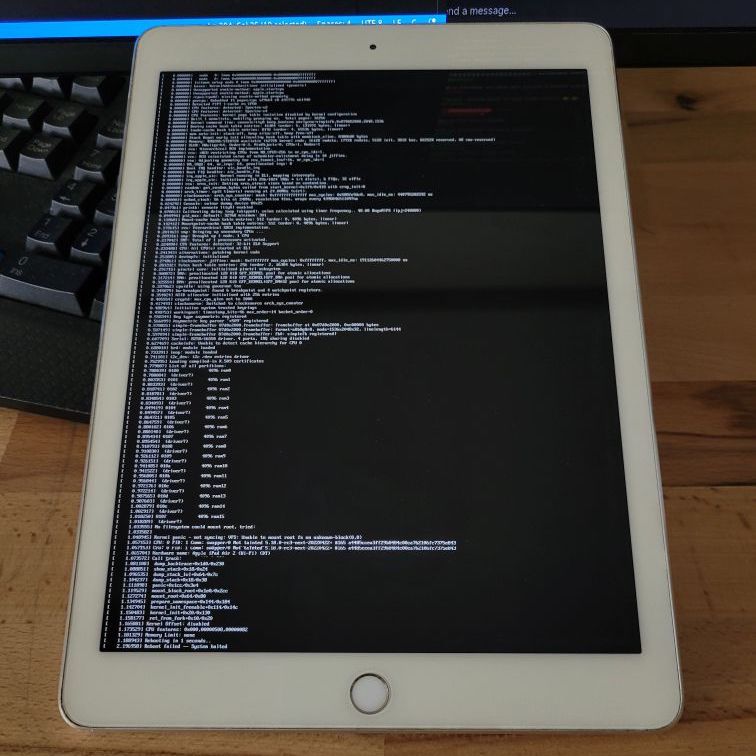
Enlarge / Linux booting up on an old iPad Air 2. (credit: Konrad Dybcio)
If you have a 2013- or 2014-era iPad sitting around unused because it’s not getting updates from Apple anymore and has stopped running the apps you need, some developers are working on an alternative software solution for you. Developer Konrad Dybcio and a Linux enthusiast going by “quaack723” have collaborated to get Linux kernel version 5.18 booting on an old iPad Air 2, a major feat for a device that was designed to never run any operating system other than Apple’s.
The project appears to use an Alpine Linux-based distribution called “postmarketOS,” a relatively small but actively developed distribution made primarily for Android devices. Dybcio used a “checkm8” hashtag in his initial tweet about the project, strongly implying that they used the “Checkm8” bootrom exploit published back in 2019 to access the hardware. For now, the developers only have Linux running on some older iPad hardware using A7 and A8-based chips—this includes the iPad Air, iPad Air 2, and a few generations of iPad mini. But subsequent tweets imply that it will be possible to get Linux up and running on any device with an A7 or A8 in it, including the iPhone 5S and the original HomePod.
This isn’t the only project devoted to running Linux on Apple’s hardware. One project, Asahi Linux, has been dedicated to reverse-engineering support for the M1 chips in Apple’s Macs and sending the patches upstream so that they can be integrated into the Linux kernel. Another, Project Sandcastle, has a build of Android up and running on an iPhone 7. Apps like iSH will give you a Linux shell running on top of iOS or iPadOS—not the same as running Linux on the hardware directly, but useful in some circumstances.