NASA releases first image from an in-focus Webb telescope

Enlarge / With better alignment, the test star has been joined by a whole host of background stars and galaxies. (credit: NASA/STScI)
Today, NASA announced that it has successfully completed two further steps to align the mirrors of the Webb telescope. The resulting performance indicates that Webb will meet or exceed its design goals. “So far, we’re finding that the performance is as good [as] or better than our most optimistic projections,” said Lee Feinberg, the Webb optical telescope element manager.
The announcement was accompanied by a spectacular image that showed a sharp focus on the target star and included many in-focus galaxies in the backdrop.
Get in line
The Webb telescope’s primary mirror is made up of an array of 18 individual segments that, once properly aligned, will act as a single large mirror. The initial steps of mirror alignment involved identifying the images from each segment and bringing those images together at a single point. That work was completed back in February. At this point, the light was all gathered in one place, but it wasn’t necessarily taking an equal path from each segment, meaning the segments weren’t acting as a single mirror.
Microsoft accidentally reveals that it is testing ads in Windows Explorer
Enlarge (credit: Aurich Lawson / Ars Technica)
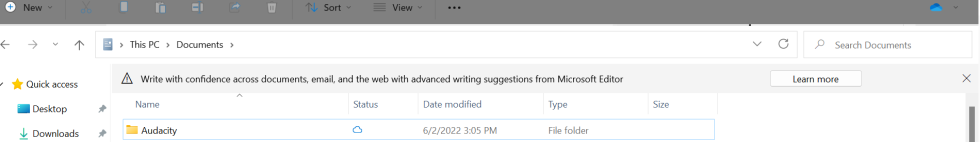
Windows 11 testers are regularly finding new Windows 11 features that Microsoft wasn’t ready to show anyone yet. Sometimes that means digging up a new Task Manager or tabs for the File Explorer. And sometimes it means finding advertisements for other Microsoft products as you browse your own locally stored files.
Microsoft MVP Florian Beaubois found an example of the latter when he saw an ad promoting Microsoft Editor while viewing his Documents folder in a Windows 11 build. In a statement to The Verge, Microsoft Senior Program Manager Brandon LeBlanc acknowledged that the banner ad was genuine, but he said that it had been “experimental” and that it “was not intended to be published externally and was turned off.”
As The Verge notes, “we didn’t mean for anyone to see that” is not a promise to never run ads in Windows Explorer, and Microsoft’s behavior around its Edge browser, Microsoft account requirements, and prompts to try OneDrive and Microsoft 365 all indicate that the company has no problem with this kind of aggressive internal promotion of its own products and services. It’s an unfortunate reality that comes with using a big company’s products—you’ll get promo notifications for Apple TV+ on your iPhone, suggestions that you switch to Chrome when you’re using Gmail, or prominent ads for Alexa-based products every time you try to buy a $6 cable on Amazon.
Google Domains is out of beta after seven years

Google Domains is officially out of beta after a whopping seven years. Some Google products start up (and shut down) at a breathtaking pace, but Domains got an old-school, multi-year-long beta, just like in the early days of Gmail. Domains launched to everyone in the US in 2015 and has since expanded to support 26 countries.
Google Domains is a simple service that lets you buy a domain, with over 300 different domain endings. It’s not the cheapest registrar available, but the interface is great, and the fees for common TLDs are just $12 per year, every year, without any of the extra fees or renewal increases that some sites charge. Registrant privacy is free, as is access to Google’s DNS.
Of course, you can protect all your domain settings behind the two-factor authentication security settings you have on a regular Google account. You can forward emails to your consumer Gmail inbox or use the domain to start a Google Workspace organization. If you’re using a Google Cloud or Ads product, Domains supports easy domain verification with one of those services, too. Google does so much stuff on the Internet that having a service like this to direct customers to just makes sense.
Free Python Crash Course
No-code development platform Webflow eyes the enterprise with $120M fundraise

Webflow is eyeing a bigger piece of the enterprise no code development pie, and to help, it has raised $120 million in a round of funding.Read More
Hidden Door reveals its AI-powered narrative game platform

Hidden Door, a new studio, today announced its launch. It also announced its first product.Read More
Lila Games raises $10M round for free-to-play mobile game studio in India
Python Get Last Element in List – How to Select the Last Item
Researcher uses Dirty Pipe exploit to fully root a Pixel 6 Pro and Samsung S22

Enlarge (credit: Getty Images)
A researcher has successfully used the critical Dirty Pipe vulnerability in Linux to fully root two models of Android phones—a Pixel 6 Pro and Samsung S22—in a hack that demonstrates the power of exploiting the newly discovered OS flaw.
The researcher chose those two handset models for a good reason: They are two of the few—if not the only—devices known to run Android version 5.10.43, the only release of Google’s mobile OS that’s vulnerable to Dirty Pipe. Because the LPE, or local privilege escalation, vulnerability wasn’t introduced until the recently released version 5.8 of the Linux kernel, the universe of exploitable devices—whether mobile, Internet of Things, or servers and desktops—is relatively small.
Behold, a reverse shell with root privileges
But for devices that do package affected Linux kernel versions, Dirty Pipe offers hackers—both benign and malicious—a platform for bypassing normal security controls and gaining full root control. From there, a malicious app could surreptitiously steal authentication credentials, photos, files, messages, and other sensitive data. As I reported last week, Dirty Pipe is among the most serious Linux threats to be disclosed since 2016, the year another high-severity and easy-to-exploit Linux flaw named Dirty Cow came to light.